Assess your database security using this straightforward manual
To ensure your database is impervious to hackers, adopt their perspective. What valuable data would attract a hacker's attention? How might they attempt to obtain it? Databases come in various forms, and there are numerous hacking techniques, but most hackers focus on cracking the root password or exploiting known vulnerabilities. With a grasp of SQL and fundamental database concepts, you can penetrate a database.
Procedures
Exploiting through SQL Injection
Determine database vulnerability. Proficiency with database queries is essential for this method. Access the database's web interface login screen via your browser and input a ’ (single quote) into the username field. Click “Login.” If an error message appears, such as “SQL Exception: quoted string not properly terminated” or “invalid character,” the database is susceptible to SQL injections.
Determine the Number of Columns. Head back to the database's login page (or any URL ending in “id=” or “catid=”) and click on the browser's address box. After the URL, type
order by 1, then hit ↵ Enter. Increase the number to 2 and hit ↵ Enter. Continue increasing until you encounter an error. The correct number of columns is the one before the error occurs.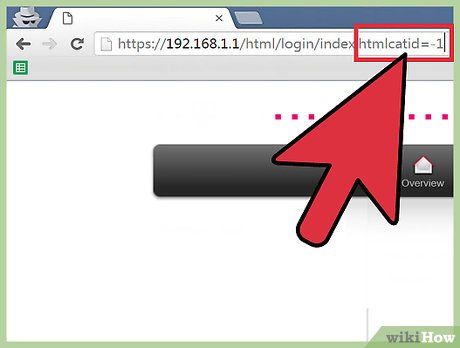
Identify Query-Accepting Columns. Amend the URL in the address bar by changing
catid=1 or id=1 to catid=-1 or id=-1. Hit the space bar and input union select 1,2,3,4,5,6 (if there are 6 columns). Each number should increment up to the total number of columns, separated by commas. Press ↵ Enter to view the query-accepting columns.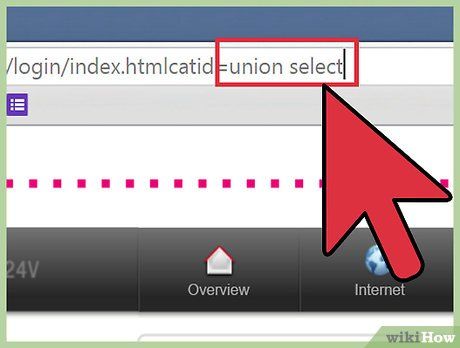
Inject SQL Statements into Columns. Suppose you wish to retrieve the current user's information and intend to inject into column 2. Remove everything after the id=1 in the URL and add a space. Then, enter
union select 1,concat(user()),3,4,5,6--. Press ↵ Enter to reveal the current database user's name on the screen. Utilize SQL statements to retrieve desired information, such as lists of usernames and passwords for cracking.Breaking the Database Root Password
Attempt Login as Root with Default Password. Certain databases lack a default root (admin) password, enabling access by leaving the password field blank. Others have easily discoverable default passwords, often found in database tech support forums.
Attempt Common Passwords. If the admin has protected the account with a password (which is likely), try common username/password combinations. Some hackers share lists of cracked passwords obtained using auditing tools. Experiment with different username and password combinations.
Utilize a Password Auditing Tool. Various tools can attempt thousands of dictionary words and alphanumeric combinations through brute force until the password is discovered. Tools like DBPwAudit (for Oracle, MySQL, MS-SQL, and DB2) and Access Passview (for MS Access) are widely used. Ensure to research extensively before downloading any tool.
Executing Database Exploits
Discover an Exploit to Execute. Sectools.org has compiled security tools, including exploits, for over a decade. Their tools are trustworthy and commonly used by system administrators worldwide. Alternatively, you can explore reputable sites like www.exploit-db.com for database-specific exploits.
Locate a Vulnerable Network through Wardriving. Wardriving involves scanning networks while traveling around an area, typically using tools like NetStumbler or Kismet. While wardriving itself is legal, any illegal activities conducted on discovered networks are not.
Utilize the database exploit from the vulnerable network. If you're engaging in unauthorized activities, it's unwise to do so from your own network. Connect wirelessly to one of the open networks you discovered while wardriving and execute the exploit you've researched and selected.
Pointers
- Always safeguard sensitive data behind a firewall.
- Ensure your wireless networks are password-protected to prevent wardrivers from exploiting your home network.
- Connect with other hackers and seek advice. Sometimes, the most valuable hacking knowledge isn't publicly available.
Cautions
- Illegally accessing a database you don't own is against the law.
- Never attempt illegal access to a system from your own network.
- Understand the laws and consequences of hacking in your jurisdiction.
