Concerned about your network's security or that of others? Safeguarding your router from unauthorized access is essential for a secure network. Nmap, also known as Network Mapper, is a key tool for this task. It scans a target and provides insights into open and closed ports, among other details. Security experts rely on Nmap to assess network security. To get started with Nmap, follow Step 1 below.
Steps
Utilizing Zenmap
Get the Nmap installer. You can find it for free on the developer's official website. It's advisable to download directly from the developer to avoid potential malware or counterfeit files. The Nmap installer includes Zenmap, a user-friendly graphical interface, facilitating scans for beginners without the need for command-line knowledge.
- Zenmap is compatible with Windows, Linux, and Mac OS X. Installation files for all these systems are available on the Nmap website.
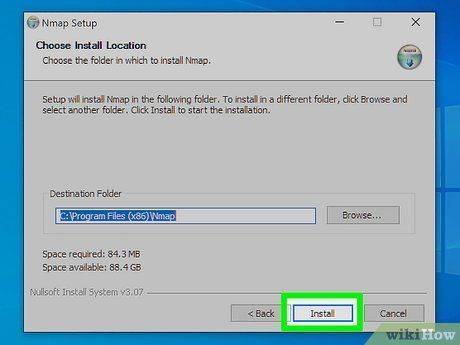
Install Nmap. Once the download is complete, run the installer. During installation, you'll be prompted to choose components. For optimal Nmap functionality, keep all options selected. Rest assured, Nmap does not include any adware or spyware.
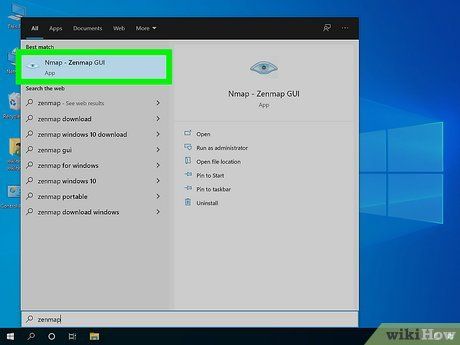
Launch the “Nmap – Zenmap” GUI program. If you've kept default settings during installation, you'll find its icon on your desktop. Alternatively, check your Start menu. Opening Zenmap will initiate the program.
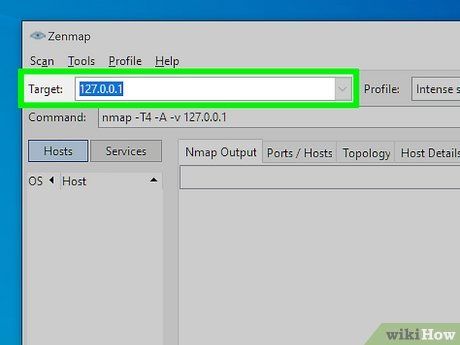
Specify the target for your scan. Zenmap simplifies scanning. To begin, define your target. This could be a domain (example.com), an IP address (127.0.0.1), a network (192.168.1.0/24), or a combination.
- Depending on scan intensity and target, conducting Nmap scans may violate your ISP terms and local laws. Always verify before scanning beyond your network.
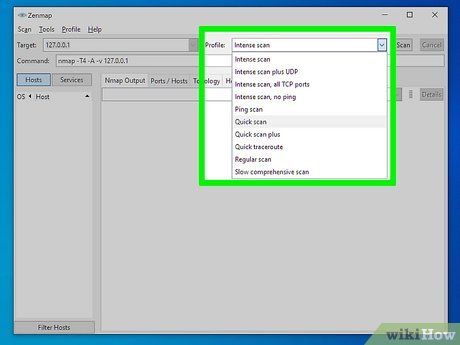
Select your Profile. Profiles offer preset modifier groupings altering scan parameters. They streamline scan setup, eliminating the need for command-line input. Choose the profile suiting your requirements:
- Intense scan - Comprehensive with OS and version detection, script scanning, traceroute, and aggressive timing. This is considered intrusive.
- Ping scan - Simply detects online targets, without port scanning.
- Quick scan - Faster due to aggressive timing and limited port scanning.
- Regular scan - Standard Nmap scan, returning ping and open ports on the target.
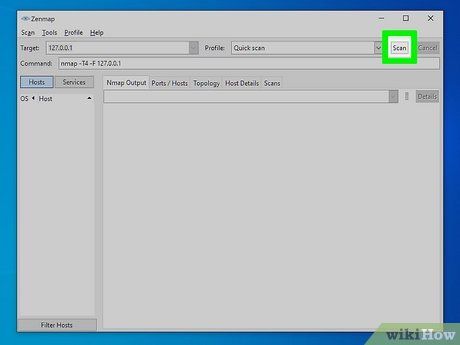
Initiate the scan by clicking Scan. Scan results will display in the Nmap Output tab. Scan duration depends on profile, target distance, and network configuration.
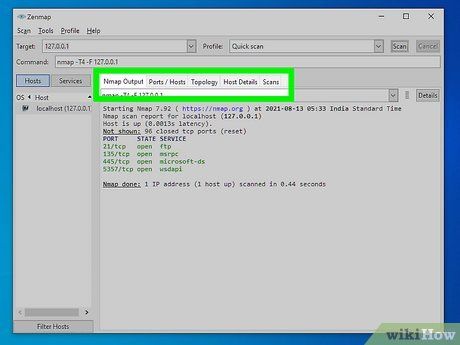
Review your scan results. Upon completion, you'll find the message “Nmap done” at the bottom of the Nmap Output tab. From there, you can examine the results based on your scan type. While the main tab lists all results, specific data can be viewed in other tabs.
- Ports/Hosts - Displays port scan results, along with associated services.
- Topology - Shows the traceroute for your scan, revealing the number of hops to your target.
- Host Details - Provides a summary of target information gathered through scans, including port count, IP addresses, hostnames, operating systems, and more.
- Scans - Stores previously-run scan commands, facilitating quick rescanning with predefined parameters.
Employing the Command Line Interface
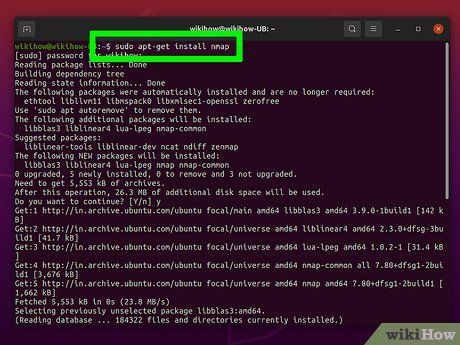
Install Nmap. Before utilizing Nmap via command line, installation is necessary. Nmap is freely available from the developer. Follow instructions tailored to your operating system:
-
Linux - Obtain and install Nmap from your repository. It's accessible through major Linux repositories. Utilize the appropriate command for your distribution:
- Red Hat, Fedora, SUSE
rpm -vhU https://nmap.org/dist/nmap-6.40-1.i386.rpm(32-bit) ORrpm -vhU https://nmap.org/dist/nmap-6.40-1.x86_64.rpm(64-bit) - Debian, Ubuntu
sudo apt-get install nmap
- Red Hat, Fedora, SUSE
-
Windows - Download the Nmap installer from the developer's website. It's recommended to download directly to avoid malware or counterfeit files. The installer streamlines command-line Nmap tool installation, eliminating manual extraction.
- If you prefer excluding the Zenmap GUI, deselect it during installation.
- Mac OS X – Obtain the Nmap disk image from the developer's website. Download directly to avoid malware or counterfeit files. Use the included installer for OS X 10.6 or later.
Access your command line interface. Nmap commands are executed from the command line, with results displayed below. Utilize variables to adjust scans. The scan can be initiated from any directory on the command line.
- Linux - Access the terminal via GUI or distribution-specific methods.
- Windows - Access via Windows key + R, then “cmd” in the Run field. Windows 8 users can use Windows key + X and select Command Prompt. Scans can be run from any directory.
- Mac OS X - Access the Terminal application in the Utility subfolder of Applications.
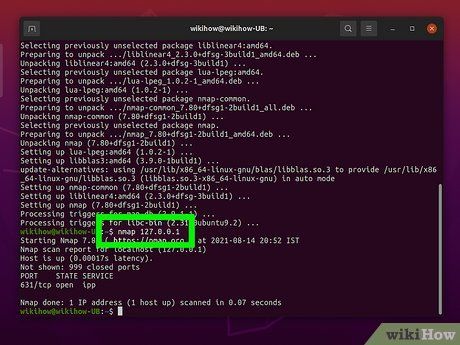
Initiate a port scan. To perform a basic scan, type
nmap <target>. This initiates a ping and port scan, easily detected. Results are displayed on-screen. You may need to scroll to view all results.
- Depending on scan intensity and target, Nmap scans may breach ISP terms and local laws. Always verify before scanning beyond your network.
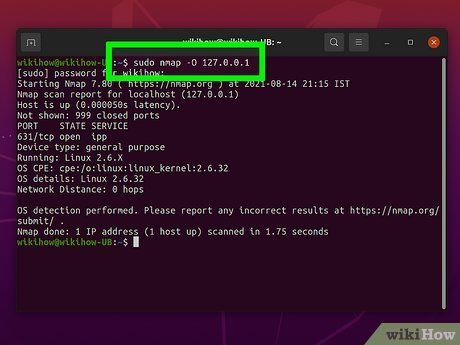
Execute a customized scan. Command line variables allow you to adjust scan parameters, yielding either more comprehensive or less detailed outcomes. Altering these variables affects the scan's intrusiveness. You can incorporate multiple variables by separating them with spaces. Variables precede the target:
nmap <variable> <variable> <target>
- -sS - SYN stealth scan. Less detectable than a standard scan but potentially slower. Some modern firewalls can detect this.
- -sn - Ping scan. Disables port scanning, only checking if the host is online.
- -O - Operating system scan. Attempts to determine the target's operating system.
- -A - Enables several commonly used scans: OS detection, version detection, script scanning, and traceroute.
- -F - Activates fast mode, reducing scanned ports.
- -v - Displays more information in results, enhancing readability.
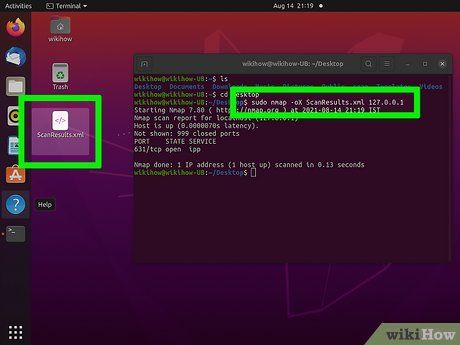
Export scan results to an XML file. Configure your scan results to be saved as an XML file for easy viewing in any web browser. Use the -oX variable and specify a filename for the XML file. Example command:
nmap –oX Scan Results.xml <target>.
- The XML file will be saved in your current working directory.
Insights
-
Not receiving responses from the target? Try adding the '-P0' switch to your scan. This forces Nmap to proceed with the scan, even if it suspects the target's absence. Useful for targets behind firewalls.
-
Curious about scan progress? Hit the spacebar or any key while the scan is ongoing to check Nmap's status.
-
If your scan seems endless (lasting twenty minutes or more), consider adding the '-F' switch to scan only the most commonly used ports.
Cautions
- If you frequently conduct Nmap scans, anticipate inquiries from your Internet Service Provider (ISP). Some ISPs actively monitor Nmap activity, and Nmap isn't exactly inconspicuous. Being a well-known tool used by hackers, you might need to provide explanations.
- Ensure you have authorization to scan the target! Scanning www.whitehouse.gov is a risky move. For practice, consider scanme.nmap.org. It's a test system provided by the Nmap author, designed for safe scanning.
