Impress your friends by faking your hacking abilities
Do you wish to be perceived as a computer genius and expert hacker? Since hacking necessitates extensive computer knowledge, observers are often impressed when they witness what they perceive as hacking. You don't need to engage in any illegal activities to make others think you're hacking—you can even simulate hacking using only the Windows Command Prompt (CMD) or a web browser. Continue reading for advice on appearing like a hacker through basic terminal commands and simulators.
Key Information
- Utilize Command Prompt (cmd) on Windows or Terminal on a Mac to execute non-threatening yet intimidating commands that mimic hacking.
- On Windows, you can craft a batch script that creates the appearance of hacking into a system and downloading files in real-time.
- Websites such as GeekTyper and Hacker Typer showcase authentic-looking hacker interfaces in your browser.
Procedure
Using Command Prompt or Terminal
Access Command Prompt (PC) or Terminal (Mac).
- On Windows, enter cmd in the search bar and select Command Prompt from the results.
- For Mac, go to Launchpad, search for terminal, and choose Terminal from the results.
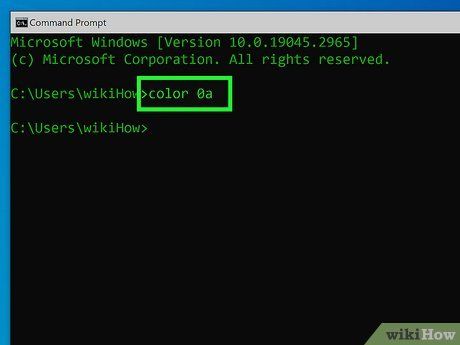
Adjust text color. Opt for bright green or blue text on a black background for that authentic hacker vibe:
- Windows: Type color 0A and press Enter for green text on black. Use color //? to see all color options.
- Mac: Navigate to Terminal > Settings > Profiles, and choose the Homebrew profile for black background with green and blue text.
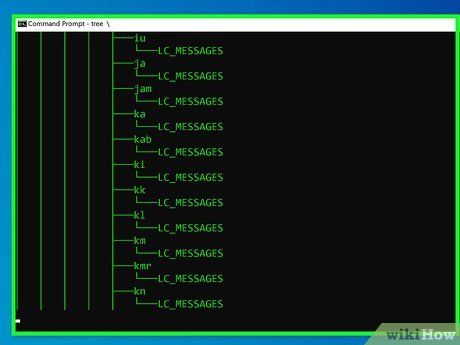
Simulate hacking using Command Prompt or Terminal. Execute impressive yet harmless commands:
- Windows: Enter commands like tree, dir , ipconfig /all, and ping -t google.com.
- Mac: Use commands like top, ps -ely, ls -R /, and ping google.com.
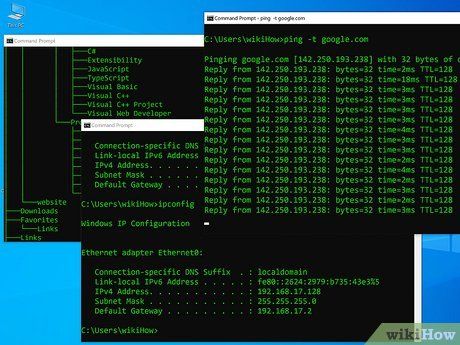
Switch between commands and windows. Open multiple Command Prompt or Terminal windows and execute various commands simultaneously to create the illusion of complex processes.
Creating a Batch File in Windows
Launch Notepad. This method involves crafting a batch file to simulate a hacking scenario where you appear to access a computer and download its files. Batch files execute a sequence of commands, and you can easily create one in Notepad without any coding knowledge by using provided code snippets.
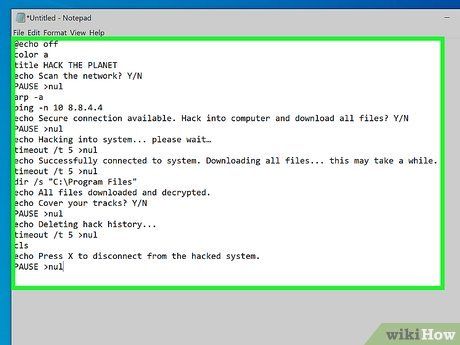
Compose the script for your .bat file in Notepad. The provided code sets up a window with green font labeled 'HACK THE PLANET.' You can customize the title as per your preference. The code also executes a series of benign commands like ping, arp, and dir with simulated hacker-like messages.
-
Insert the following code into your Notepad file:
@echo off
color a
title HACK THE PLANET
echo Scan the network? Y/N
PAUSE >nul
arp -a
ping -n 10 8.8.4.4
echo Secure connection available. Hack into computer and download all files? Y/N
PAUSE >nul
echo Hacking into system... please wait…
timeout /t 5 >nul
echo Successfully connected to system. Downloading all files... this may take a while.
timeout /t 5 >nul
dir /s 'C:Program Files'
echo All files downloaded and decrypted.
echo Cover your tracks? Y/N
PAUSE >nul
echo Deleting hack history...
timeout /t 5 >nul
cls
echo Press X to disconnect from the hacked system.
PAUSE >nul
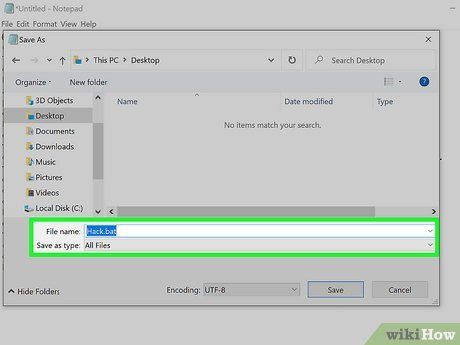
Save your file as a .bat file. Navigate to the File menu, choose Save as, and name your file hack.bat. This will convert your file from a text document to a batch file.
- Storing the file on your desktop simplifies execution.
Execute your .bat file. Double-click your .bat file in its directory to open a window resembling a complex computer process, akin to a hacker's activity.
- If your Windows installation isn't on the C drive, you may encounter an error. In such cases, substitute the 'C' in 'C:Program Files' with the appropriate drive letter. You can also modify this path to any folder, such as a fictitious directory containing files like 'Passwords' or 'Private Information.'
Exploring Websites
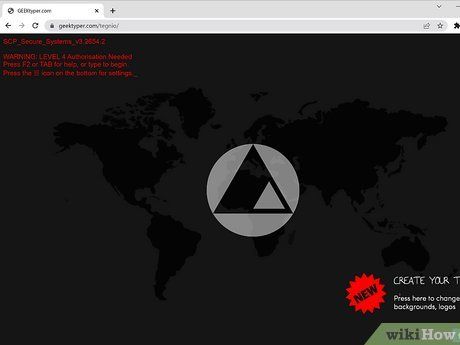
Geektyper. Explore https://www.geektyper.com for an immersive simulated hacking experience. This site offers one of the most authentic hack-simulating interfaces. After landing on the homepage, select a theme and start typing to generate hacker-like text. You can also interact with folders to simulate complex but fake processes.
- Select a theme and navigate between the text and processes generated by keystrokes by clicking on folders and windows.
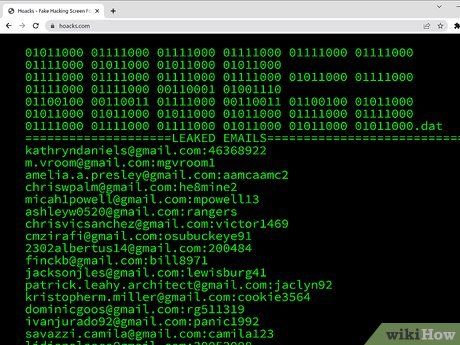
HackerTyper. Visit https://hackertyper.net/ using your web browser. This site generates hacker-like text at an impressive pace, sure to astonish onlookers. However, one drawback is its rapid generation of fake hacker code, which might diminish the intended effect when tricking your friends.
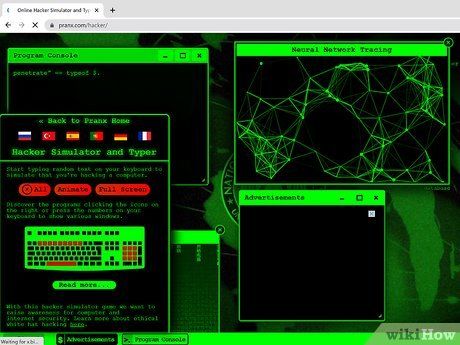
Pranx Hacker. Head to https://pranx.com/hacker to access this hacker simulator. It's ideal for running in the background while you multitask, creating the illusion of hacking. The site presents a simulated computer desktop with windows displaying falling Matrix-style text, ominous code, and fictitious programs like Bitcoin Miner and Nuclear Plant (rest assured, they're not real).
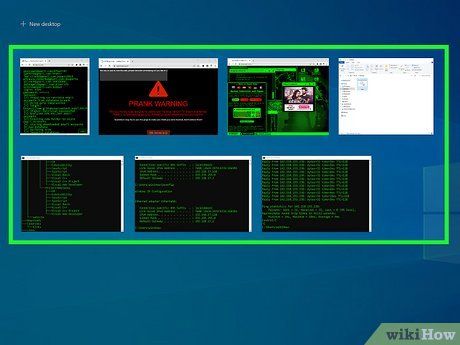
Manage multiple sites in separate windows. Each site offers a distinct ambiance and generates varied styles of fake code/hacker text. Quickly switch between open windows by holding the Alt key and pressing Tab ↹ to cycle through your options. Type a few keystrokes in each window before switching to a new fake-hacking browser window for enhanced authenticity. To switch between tabs within the same window, press Ctrl+Tab ↹.
- Experiment with different window arrangements, or keep some windows open in the background to give the impression of being a skilled hacker.
Utilizing Linux (Ubuntu & Debian)

Launch a new Terminal session. Use Ctrl + Alt + T to open one.
- If Linux isn't yet installed, refer to this useful guide.
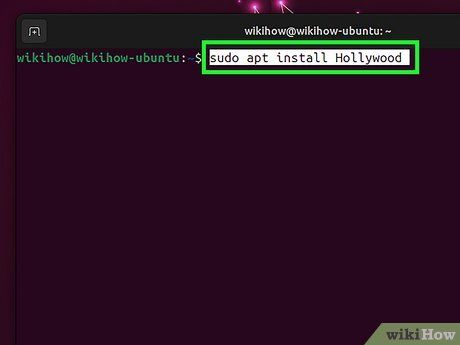
Enter sudo apt install Hollywood and hit ↵ Enter. This command installs Hollywood, a phony hacking tool, onto your Linux system. Hollywood boasts a menacing appearance, perfect for impressing your peers.
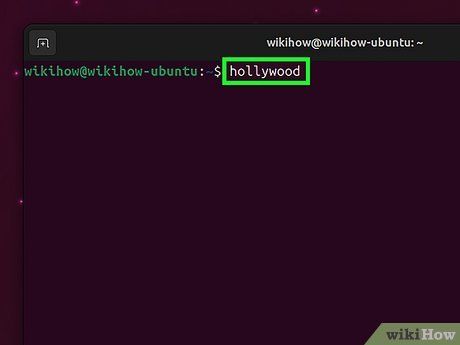
Type hollywood and press ↵ Enter. To maximize the effect, enlarge your Terminal window to full-screen.
Pointers
Cautionary Notes
- Individuals knowledgeable in computer systems and coding can promptly discern whether you're genuinely engaged in activity or merely theatrics. Therefore, choose your audience for your 'hacking' demonstration wisely.
- Some adults might genuinely believe you're hacking, so exercise caution and avoid getting into trouble.
