 There's nothing worse than discovering your computer is infected with a dangerous virus.
@iStockphoto.com/Olaf Loose
There's nothing worse than discovering your computer is infected with a dangerous virus.
@iStockphoto.com/Olaf LooseComputer viruses are a real menace. Some can completely erase data from your hard drive, clog up a computer network for hours, transform a harmless machine into a zombie, and then replicate themselves, sending copies to other devices. If you've never experienced a virus attack, you might not fully understand the concern. However, it's easy to see why people are worried—according to Consumer Reports, computer viruses were responsible for contributing to $8.5 billion in consumer losses in 2008 [source: MarketWatch]. Though just one form of online threat, computer viruses are undoubtedly among the most notorious.
Computer viruses have existed for many years. In fact, as early as 1949, scientist John von Neumann proposed the idea of self-replicating programs [source: Krebs]. The computer industry was still in its infancy, and yet someone had already figured out how to sabotage its growth. It would take several more decades before programmers, later known as hackers, began creating actual computer viruses.
While early programmers created virus-like software for large computer systems, it was the arrival of the personal computer that truly brought viruses into the public spotlight. A doctoral student named Fred Cohen became the first to describe self-replicating programs designed to modify computers, calling them viruses—a name that has remained ever since.
Back in the early 1980s, viruses relied on human intervention to spread. A hacker would save the virus onto floppy disks and distribute them to others. It wasn’t until modems became widespread that virus transmission really became an issue. Today, when we think of computer viruses, we often picture ones that spread over the Internet. They might infect systems through e-mail attachments or malicious web links, and they can spread far more quickly than the viruses of the past.
Let's dive into a look at 10 of the most devastating computer viruses that have crippled systems. First up is the Melissa virus.
10: Melissa
 A courtroom image of David L. Smith, the suspected creator of the Melissa virus.
Daniel Hulshizer/AFP/Getty Images
A courtroom image of David L. Smith, the suspected creator of the Melissa virus.
Daniel Hulshizer/AFP/Getty ImagesIn the spring of 1999, a man named David L. Smith developed a computer virus using a Microsoft Word macro. He designed it to spread via e-mail messages. Smith named the virus 'Melissa,' after an exotic dancer from Florida [source: CNN].
Instead of dancing, the Melissa virus lures victims with an e-mail message saying, 'Here is that document you asked for, don’t show it to anyone else.' Once the recipient opens it, the virus activates, replicates itself, and sends copies to the first 50 contacts in their e-mail address book.
The virus spread quickly after Smith released it. The U.S. government became highly interested in his actions — FBI officials told Congress that the Melissa virus "caused chaos across government and private sector networks" [source: FBI]. The overwhelming surge in e-mail traffic led some companies to shut down their e-mail systems until the virus was contained.
After a lengthy trial, Smith lost his case and was sentenced to 20 months in prison. The court also imposed a $5,000 fine and prohibited Smith from accessing computer networks without prior court approval [source: BBC]. While the Melissa virus didn’t destroy the Internet, it was one of the first viruses to capture widespread public attention.
Types of Viruses
This article will explore several different categories of computer viruses. Here’s a brief overview of what’s to come:
- The term 'computer virus' generally refers to programs that alter a computer’s operation (including causing damage) and can replicate themselves. A true computer virus needs a host program to function properly—Melissa used a Word document as its host.
- A worm, however, doesn’t rely on a host program. It’s a standalone application that can duplicate itself and spread through computer networks.
- Trojan horses are programs that appear to do one thing but actually perform something else. Some can harm the victim's hard drive, while others create backdoors that let remote users access the victim's computer system.
Next, let’s explore a virus with a sweet name but a devastating impact on its victims.
Among the earliest viruses to infect personal computers were the Apple Viruses, which specifically targeted Apple II computers.
9: ILOVEYOU
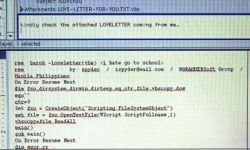 A screenshot depicting the ILOVEYOU computer virus
Robyn Beck/AFP/Getty Images
A screenshot depicting the ILOVEYOU computer virus
Robyn Beck/AFP/Getty ImagesA year after the Melissa virus struck the Internet, a new digital threat surfaced from the Philippines. Unlike Melissa, this new menace was a worm—a self-replicating, standalone program. It was named ILOVEYOU.
The ILOVEYOU virus spread across the Internet via e-mail, much like the Melissa virus. The e-mail’s subject claimed it was a love letter from a secret admirer. The trouble started with an attachment: the original worm file was named LOVE-LETTER-FOR-YOU.TXT.vbs. The vbs extension indicated the programming language used to create the worm: Visual Basic Scripting [source: McAfee].
According to anti-virus software company McAfee, the ILOVEYOU virus launched a wide array of attacks:
- It created multiple copies of itself and concealed them in various folders on the victim's hard drive.
- It modified the victim’s registry keys by adding new files.
- It replaced different types of files with copies of itself.
- It spread via both Internet Relay Chat (IRC) and e-mail.
- It downloaded a file named WIN-BUGSFIX.EXE from the Internet and executed it. Contrary to its name, the file wasn’t a bug-fixer—it was a password-stealing program that sent confidential information to the hacker’s e-mail address.
Who was behind the ILOVEYOU virus? Some speculate it was Onel de Guzman from the Philippines. Filipino authorities investigated him on theft charges—however, at the time, the Philippines lacked laws addressing computer espionage or sabotage. Due to insufficient evidence, the charges were dropped. De Guzman neither confirmed nor denied his involvement. Some estimates claim the ILOVEYOU virus caused $10 billion in damages [source: Landler].
Now that the love affair is over, let’s shift focus to one of the most widespread viruses that ever hit the Web.
As if viruses, worms, and Trojan horses weren't enough, we also face the menace of virus hoaxes. These are fake viruses—they don’t actually harm or replicate. Instead, their creators aim to make people and media treat them as real threats. While they may not be immediately dangerous, hoax viruses pose a problem. Like the story of the boy who cried wolf, these hoaxes can cause people to ignore warnings about genuine threats.
8: The Klez Virus
 Luckily for users, there’s no shortage of antivirus software options available.
Joe Raedle/Getty Images
Luckily for users, there’s no shortage of antivirus software options available.
Joe Raedle/Getty ImagesThe Klez virus marked a new milestone for computer viruses, raising the stakes for future threats. Emerging in late 2001, it had several variations that continued to trouble the Internet for months. The core Klez worm would infect a victim’s computer through an e-mail, replicate itself, and then spread to the people in the victim’s address book. Some variations of the Klez virus carried additional malicious programs capable of rendering a victim’s computer unusable. Depending on the version, the Klez virus could function as a regular computer virus, worm, or Trojan horse. Some versions could even disable virus-scanning software and masquerade as a virus-removal tool [source: Symantec].
Soon after the Klez virus appeared on the Internet, hackers made tweaks to it, significantly boosting its effectiveness. Like its predecessors, it would scour a victim's address book and forward itself to contacts. However, it added a new twist: it could pick a name from the address book and use it in the "From" field of the email. This is known as spoofing, where the email seems to come from one source, but in reality, it’s originating from another.
Spoofing an email address serves a few purposes. First, it makes it difficult for the recipient to block the sender, since the email is not really coming from the address shown in the "From" field. A Klez worm designed to spam people with multiple emails could quickly overwhelm an inbox, because the recipient wouldn’t be able to pinpoint the actual source of the problem. Additionally, the recipient might recognize the name in the "From" field, making them more likely to open the email.
Antivirus Software
Having an antivirus program on your computer and keeping it up to date is essential. However, using more than one antivirus suite is not recommended, as they could interfere with each other. Below are a few examples of antivirus software suites:
- Avast Antivirus
- AVG Anti-Virus
- Kaspersky Anti-Virus
- McAfee VirusScan
- Norton AntiVirus
In 2001, several significant computer viruses made their appearance. Up next, we’ll dive into the details of Code Red.
7: Code Red and Code Red II
 The CERT Coordination Center at Carnegie Mellon University issued a public advisory warning about the threats posed by the Code Red virus.
Chris Hondros/Getty Images
The CERT Coordination Center at Carnegie Mellon University issued a public advisory warning about the threats posed by the Code Red virus.
Chris Hondros/Getty ImagesThe Code Red and Code Red II worms emerged in the summer of 2001. These worms exploited a vulnerability in the operating systems of machines running Windows 2000 and Windows NT. The issue was a buffer overflow problem, which occurs when a system receives more data than its memory buffers can handle, causing it to overwrite adjacent memory.
The initial Code Red worm launched a distributed denial of service (DDoS) attack against the White House. This meant that every infected computer tried to connect to the White House’s Web servers simultaneously, overwhelming the system.
When the Code Red II worm infects a Windows 2000 machine, the computer no longer follows the owner's commands. This is because the worm creates a backdoor into the operating system, enabling a remote attacker to control the machine. In technical terms, this is referred to as a system-level compromise, and it spells trouble for the computer’s owner. The virus creator can extract sensitive information from the infected computer or even use it to carry out criminal activities. As a result, the victim not only faces a compromised computer but may also be wrongfully implicated in crimes they didn’t commit.
Although Windows NT machines were also vulnerable to the Code Red worms, the impact on these systems wasn’t as severe. Web servers running Windows NT may have experienced more frequent crashes, but that was the extent of the damage. When compared to the far-reaching problems faced by Windows 2000 users, these issues were relatively minor.
Microsoft released patches to address the security flaws in Windows 2000 and Windows NT. After these patches were applied, the original worms could no longer infect a Windows 2000 system. However, the patches did not remove any viruses from already-infected machines, meaning that victims had to manually clean their systems.
If your computer has been infected with a virus, your next steps depend on the specific virus. Many antivirus programs can remove viruses from an infected system. However, if the virus has caused damage to files or data, you may need to restore from backups. It's crucial to back up your data frequently. For worms like the Code Red, it is often wise to fully reformat the hard drive and start fresh, as some worms can introduce additional malicious software that antivirus programs might miss during a simple scan.
6: Nimda
 The Symbian Skull Virus targets mobile phones, causing them to display a series of skull images, as seen here.
The Symbian Skull Virus targets mobile phones, causing them to display a series of skull images, as seen here.One of the major viruses that emerged on the Internet in 2001 was the Nimda worm (admin spelled backward). Nimda spread at an unprecedented rate, quickly becoming the fastest propagating computer virus of its time. According to TruSecure CTO Peter Tippett, it only took 22 minutes from its initial appearance on the Internet to become the most reported attack [source: Anthes].
The primary targets of the Nimda worm were Internet servers. While it could infect personal computers, its main goal was to overwhelm Internet traffic. Nimda could spread through various channels, including e-mail, allowing it to infect multiple servers rapidly and efficiently.
The Nimda worm created a backdoor into the infected machine's operating system. This allowed the attacker to access the system with the same level of permissions as the account currently logged in. If a user with limited privileges triggered the worm, the attacker would have the same restricted access. However, if the victim was an administrator, the attacker would gain full control of the machine.
As the Nimda worm spread, it caused significant strain on network systems, leading some to crash. The worm consumed more and more of the system's resources, effectively turning it into a distributed denial of service (DDoS) attack.
Phoning it In
Not all viruses target computers. Some go after other electronic devices. Here are a few examples of viruses that affected portable gadgets:
- CommWarrior targeted smartphones using the Symbian operating system (OS).
- The Skulls Virus also infected Symbian phones, replacing the home screen with images of skulls.
- RavMonE.exe was a virus that infected iPod MP3 devices manufactured between September 12, 2006, and October 18, 2006.
- Fox News reported in March 2008 that some electronic devices were sold with viruses pre-installed, which would then infect your computer when the device was synced [source: Fox News].
Next, let's explore a virus that targeted major networks, including airline systems and bank ATMs.
5: SQL Slammer/Sapphire
 The Slammer virus had a devastating impact on South Korea, causing widespread Internet disruption and leaving Internet cafes, like the one shown here, nearly empty.
Chung Sung-Jun/Getty Images
The Slammer virus had a devastating impact on South Korea, causing widespread Internet disruption and leaving Internet cafes, like the one shown here, nearly empty.
Chung Sung-Jun/Getty ImagesIn late January 2003, a new virus targeting Web servers began spreading rapidly across the Internet. Many computer networks were unprepared for the attack, which resulted in the shutdown of several crucial systems. The Bank of America's ATM network failed, 911 services in Seattle experienced outages, and Continental Airlines was forced to cancel numerous flights due to issues with electronic ticketing and check-ins.
The source of the chaos was the SQL Slammer virus, also referred to as Sapphire. Estimates suggest the virus caused damages exceeding $1 billion before patches and antivirus programs could respond [source: Lemos]. The virus's rapid spread is well documented—just minutes after infecting its first server, it began doubling its number of victims every few seconds. Within 15 minutes, nearly half of the servers supporting the Internet were compromised [source: Boutin].
The Slammer virus imparted a crucial lesson: Having up-to-date patches and antivirus software is not enough. Hackers will always seek out vulnerabilities, especially those that are not widely known. While it's vital to try to prevent viruses from infecting your system, it's equally important to have a contingency plan in place for when the worst happens.
A Matter of Timing
Certain hackers program viruses to lie dormant on a victim's machine, only to trigger an attack on a specific date. Here's a quick rundown of some notorious viruses that had time-based triggers:
- The Jerusalem virus was set to activate on every Friday the 13th, causing it to delete data from the infected computer's hard drive.
- The Michelangelo virus activated on March 6, 1992 – the same day Michelangelo was born in 1475.
- The Chernobyl virus activated on April 26, 1999, marking the 13th anniversary of the catastrophic Chernobyl disaster.
- The Nyxem virus executed its payload on the third day of every month, wiping out files from the victim's computer.
Computer viruses can leave their victims feeling powerless, exposed, and demoralized. Next, we'll explore a virus with a name that captures all of these emotions.
4: MyDoom
 The MyDoom virus led figures like U.S. Senator Chuck Schumer to suggest the creation of a National Virus Response Center.
Alex Wong/Getty Images
The MyDoom virus led figures like U.S. Senator Chuck Schumer to suggest the creation of a National Virus Response Center.
Alex Wong/Getty ImagesThe MyDoom (also known as Novarg) virus is another malicious worm that can create a backdoor in the victim's operating system. The original variant of MyDoom – there were multiple versions – was triggered in two ways. One trigger initiated a denial of service (DoS) attack on February 1, 2004. The second stopped the virus from spreading on February 12, 2004. However, even after the virus ceased its propagation, the backdoors created during the initial infections remained active [source: Symantec].
Later in 2004, a second wave of the MyDoom virus caused considerable trouble for several search engine companies. As with many other viruses, MyDoom searched infected computers for e-mail addresses to aid in its replication. But, it also sent search requests to search engines and used e-mail addresses found in the search results. This led to millions of requests flooding search engines like Google, causing slowdowns and even crashes [source: Sullivan].
MyDoom spread through both e-mail and peer-to-peer networks. Security company MessageLabs reported that at one point, one out of every 12 e-mails contained the virus [source: BBC]. Like the Klez virus, MyDoom could spoof e-mails, making it difficult to trace the origin of the infection.
Oddball Viruses
Not all viruses wreak havoc or cripple networks. Some simply cause unusual behaviors in infected computers. A well-known early example is the Ping-Pong virus, which displayed a bouncing ball graphic but caused no real harm. There are also joke programs that may trick users into thinking their computer is infected, though they are simply harmless applications that don’t replicate. When unsure, it’s always best to have an antivirus program remove the suspicious application.
Next, we will explore two viruses that were created by the same hacker: the Sasser and Netsky viruses.
3: Sasser and Netsky
 Sven Jaschan, the creator of the Sasser and Netsky viruses, departs from the Verden Court.
David Hecker/AFP/Getty Images
Sven Jaschan, the creator of the Sasser and Netsky viruses, departs from the Verden Court.
David Hecker/AFP/Getty ImagesOccasionally, creators of computer viruses evade detection. However, every so often, authorities manage to trace a virus back to its creator. This was the case with the Sasser and Netsky viruses. A 17-year-old German named Sven Jaschan developed these two worms and released them onto the Internet. Although the two viruses acted differently, their code similarities led security experts to conclude that both were crafted by the same individual.
The Sasser worm exploited a vulnerability in Microsoft Windows to infect computers. Unlike many other worms, it didn’t spread via email. Instead, after infecting a computer, the virus searched for other vulnerable machines. It would reach out to those systems, instructing them to download the virus. The virus scanned random IP addresses to locate potential targets. It also altered the victim's operating system, making it nearly impossible to shut down the computer without forcibly cutting off the power.
The Netsky virus spreads through emails and Windows networks, spoofing email addresses and propagating via a 22,016-byte file attachment [source: CERT]. As it circulates, it can lead to a denial of service (DoS) attack as systems struggle to handle the overwhelming internet traffic. At one point, experts from Sophos estimated that Netsky and its variations accounted for 25% of all viruses online [source: Wagner].
Sven Jaschan faced no jail time for his actions; he was sentenced to one year and nine months of probation. Since he was under 18 at the time of his arrest, he avoided being tried as an adult in German courts.
So far, most of the viruses we've examined have primarily targeted PCs running Windows. However, Macintosh computers are not invulnerable to virus attacks. In the following section, we will explore the first virus to target Mac systems.
Just like in Oz, where there were both good and bad witches, our world has both good and bad hackers. A common term for a hacker who aims to create viruses or compromise system security is a black hat. Some hackers participate in conventions like the Black Hat conference or Defcon to discuss the consequences of black hat activities and how these hackers exploit vulnerabilities in computer security systems to commit crimes.
2: Leap-A/Oompa-A
 We owe it to "Weird Al" Yankovic for alerting us about the notorious "Stinky Cheese" virus.
Kevin Mazur Archive 1/WireImage/Getty Images
We owe it to "Weird Al" Yankovic for alerting us about the notorious "Stinky Cheese" virus.
Kevin Mazur Archive 1/WireImage/Getty ImagesYou might have seen the Apple Mac computer ad featuring Justin "I'm a Mac" Long comforting John "I'm a PC" Hodgman. In the ad, Hodgman, infected with a virus, points out that over 100,000 viruses can threaten a computer. Long reassures him that these viruses are aimed at PCs, not Macs.
Generally, that's accurate. Mac computers enjoy a degree of protection from viruses due to a concept called security through obscurity. Apple keeps its operating system (OS) and hardware under wraps—producing both the software and hardware. This closed system makes the OS less visible. Historically, Macs have held a smaller share of the home computer market compared to PCs. Therefore, a hacker targeting Macs may not reach as many victims as those who create viruses for PCs.
However, that didn't stop at least one Mac hacker. In 2006, the Leap-A virus, also known as Oompa-A, emerged. It used the iChat instant messaging service to spread among susceptible Mac computers. Once the virus infected a system, it scanned the iChat contact list and sent a message to each person with a file disguised as an innocent JPEG image.
While the Leap-A virus didn't cause major damage to computers, it demonstrated that even Macs can fall victim to malicious software. As Macs become more widespread, we may see an increase in hackers designing specific viruses to corrupt files or disrupt network traffic. Hodgman's character might just get his turn to strike back.
We’ve come to the final entry. Which computer virus has claimed the coveted number one spot?
While computer viruses can indeed be a serious threat to systems and Internet traffic, the media often exaggerates the extent of a virus’s impact. Take, for example, the Michelangelo virus, which received a lot of media buzz despite causing relatively minimal damage. This could have inspired "Weird Al" Yankovic's song "Virus Alert." In the song, a virus named Stinky Cheese doesn't just destroy your hard drive but also forces you to endure endless Jethro Tull songs and legally change your name to Reggie.
1: Storm Worm
 Professor Adi Shamir, from the Weizmann Institute of Sciences in Israel, is a leading figure in the Anti-Spyware Coalition.
Gabriel Bouys/AFP/Getty Images
Professor Adi Shamir, from the Weizmann Institute of Sciences in Israel, is a leading figure in the Anti-Spyware Coalition.
Gabriel Bouys/AFP/Getty ImagesAt the top of our list sits the infamous Storm Worm, which was first discovered in late 2006. The public dubbed it the Storm Worm after an email with the subject line "230 dead as storm batters Europe" was found to carry the virus. Antivirus vendors have their own names for it, though. Symantec refers to it as Peacomm, while McAfee calls it Nuwar. While this can be a bit confusing, it’s worth noting that there was a separate virus from 2001 named W32.Storm.Worm, which is completely unrelated to this 2006 worm.
The Storm Worm operates as a Trojan horse, with its true payload often being a different program each time. Certain variants of this worm transform infected computers into zombies or bots, giving the attacker the ability to control them remotely. In many cases, hackers use the Storm Worm to build a botnet, which is then used to send out massive amounts of spam across the Internet.
Various versions of the Storm Worm trick users into downloading the malicious software by disguising links to fake news articles or videos. The attackers frequently modify the subject lines of their e-mails to correspond with current events. For instance, just before the 2008 Beijing Olympics, a new version of the worm circulated in e-mails with subject lines like "a new deadly catastrophe in China" or "China's most deadly earthquake." These e-mails claimed to link to relevant video or news stories, but clicking the link actually triggered the worm's download [source: McAfee].
Numerous news outlets and blogs have labeled the Storm Worm as one of the most severe virus outbreaks in recent years. By July 2007, a Postini security official reported that over 200 million e-mails containing links to the Storm Worm were detected during an attack that lasted several days [source: Gaudin]. Thankfully, not all of those e-mails resulted in the virus being downloaded.
While the Storm Worm is widespread, it isn't one of the toughest viruses to spot or remove. By maintaining updated antivirus software and being cautious about e-mails from unknown senders or suspicious links, you can significantly reduce the risk of falling victim to it.
Viruses are only one type of malware. Other malicious software includes spyware and certain forms of adware. Spyware secretly monitors a user’s actions on their computer, often recording keystrokes to gather login credentials and passwords. Adware, on the other hand, shows advertisements to users while they are using another program, such as a web browser. Some adware even includes features that give advertisers extensive access to private user information.
