For thousands of years, the necessity to hide the meaning of critical communications has driven innovation in encoding. As simpler methods became easier to decode, more sophisticated techniques emerged. Contrary to popular belief, codes and ciphers are distinct. A code replaces entire words with specific symbols or words, while a cipher substitutes individual letters with other letters or symbols. Interestingly, what most people call “codes” are actually ciphers. Decoding and deciphering have unlocked ancient scripts, with the Rosetta Stone of Ancient Egypt being a famous example. Historically, codes and ciphers have shaped political and wartime outcomes. While countless hidden message techniques exist, this overview highlights ten, complete with examples for you to explore.
10. Steganography
Steganography predates codes and ciphers, focusing on the art of concealed writing. For instance, a message could be written on paper, coated in wax, and swallowed for secrecy, only to be retrieved later. Another method involved tattooing a message on a messenger’s shaved head, allowing hair to regrow and hide the ink. The most effective steganography uses everyday objects to carry hidden messages. In England, a popular method involved marking tiny dots under specific letters in a newspaper to spell out a message. Other techniques included using the first letter of each word or invisible ink. Rival nations have even miniaturized text to a single pixel, making it nearly invisible to observers. Steganography works best when combined with codes or ciphers, as hidden messages always risk discovery.
9. ROT1

This cipher is widely known among children. Its mechanism is straightforward: every letter in the alphabet is shifted to the next one, meaning A becomes B, B turns into C, and so forth. The term “ROT1” stands for “rotate 1 letter forward through the alphabet.” For example, the phrase “I know what you did last summer” transforms into “J lopx xibu zpv eje mbtu tvnnfs.” While this cipher is entertaining and simple to use, it’s equally easy to crack by reversing the process. Though not practical for serious encryption, it’s a delightful tool for children’s games. Can you decode the message “XBT JU B DBU J TBX?”!
8. Transposition

Transposition ciphers involve rearranging letters based on a specific rule or key. For instance, words might be reversed, turning “all the better to see you with” into “lla eht retteb to ees uoy htiw.” Another method swaps every pair of letters, transforming the same message into “la tl eh eb tt re to es ye uo iw ht.” These ciphers were employed during the First World War and the American Civil War for transmitting confidential information. While complex rearrangement rules can make them appear challenging, many transposed messages can be decoded using anagrams or advanced computer algorithms that test numerous key possibilities. Try decoding this: THGINYMROTSDNAKRADASAWTI.
7. Morse Code
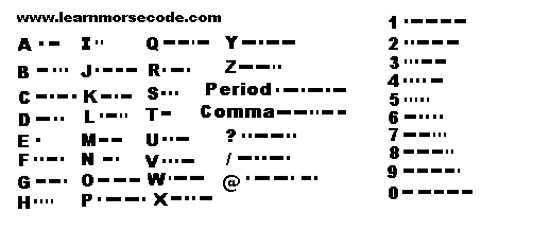
Despite its name, Morse code is technically a cipher, not a code. It represents each letter, digit (0-9), and specific punctuation marks with sequences of short and long beeps, commonly referred to as “dots and dashes.” For example, A is “•-“, B is “-•••,” and so on. Unlike most ciphers, it isn’t designed to hide messages. Morse code became essential with Samuel Morse’s telegraph, the first widely-used electric system for long-distance communication. This system relied on transmitting electric currents through wires, with dots and dashes created by turning the current on and off. The telegraph transformed media by enabling real-time reporting of global events and revolutionized warfare by facilitating instant communication with distant troops. •–• •- •-• •- -••• • •-•• •-•• ••- —
6. Caesar Shift Cipher
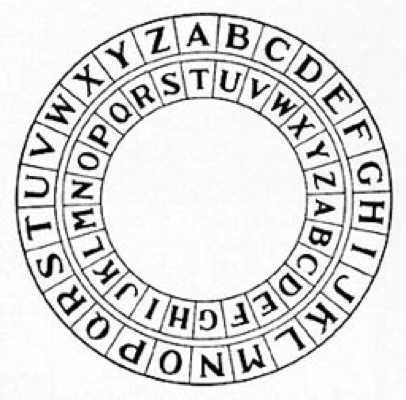
The Caesar shift cipher, attributed to Julius Caesar, encompasses 26 distinct ciphers, each corresponding to a letter in the alphabet. ROT1 is merely one variation. To decode a message, one only needs to know which specific Caesar cipher was applied. For instance, using the G cipher transforms A into G, B into H, C into I, and so forth. If the Y cipher is employed, A becomes Y, B becomes Z, C turns into A, and the pattern continues. While this cipher forms the foundation for more advanced encryption methods, it offers limited security on its own, as testing all 26 keys is relatively quick. Li bra ghflskhu wklv dqg bra nqrz lw, fods brxu kdqgv.
5. WigWag
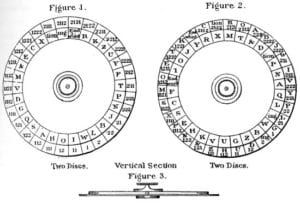
During the U.S. Civil War, battlefield communication posed significant challenges. Although telegraphs were available, their use was impractical in combat zones due to a lack of telegraph lines. Albert Myer, an American telegrapher, devised an innovative flag-waving communication system. Drawing from his knowledge of deaf communication, Myer, whose medical dissertation was titled “A New Sign Language for Deaf Mutes,” adapted telegraph code into a tactile method, allowing words to be tapped onto a person’s cheek or hand. While stationed in Texas as a medical officer in the mid-1850s, he evolved this system into the flag and torch signaling method known as ‘wig-wag.’
With both the North and South utilizing the same signaling system, encryption became essential to safeguard visual messages. Cipher disks were commonly used to encode letters before transmission via flags. Signalmen had to position themselves in highly visible locations to relay messages over long distances, while also maintaining a broad view of the battlefield.
In the wig-wag system, each letter was represented by specific flag positions or movements. Messages were encoded using a letter-number system, where numbers corresponded to flag motions. A leftward movement from the center denoted “1,” while a rightward movement signified “2.” For example, the letter A was represented as “11,” indicating two consecutive left-to-center motions. Dipping the flag forward signaled the end of a word, sentence, or message. Try decoding this: 1122/11/1111/111/211/2222.
4. Vigenère

The Vigenère cipher is more intricate than monoalphabetic substitution. It uses a keyword, such as “CHAIR,” to determine the cipher alphabet for each letter. The first letter of the message is encoded using the C cipher, the second with the H cipher, and so on, repeating the keyword as needed. For centuries, this cipher was considered unbreakable. Decoding involves guessing the keyword length. If the keyword is five letters, letters 1, 6, 11, etc., correspond to the first keyword letter, and frequency analysis helps decode them. This process repeats for letters 2, 7, 12, and so on. If the keyword length is incorrect, the process restarts with a new guess. Eoaqiu hs net hs byg lym tcu smv dot vfv h petrel tw jka.
3. Public-Key Cryptography

This cipher represents the pinnacle of modern encryption, with numerous variations in use globally. It operates using two keys: one public and one private. The public key is a large, widely accessible number, unique in that only two specific whole numbers (excluding 1 and itself) can divide it evenly. These two numbers form the private key, and their product equals the public key. For example, a public key might be 1961, with the private key being 37 and 53. While the public key encrypts messages, decryption is impossible without the private key. This method secures sensitive data, such as bank transactions, ensuring only authorized parties can access it. The security lies in the mathematical difficulty of finding divisors of large numbers. RSA Laboratories once offered rewards for identifying the divisors of specific large numbers, such as the two 50-digit divisors of 1522605027922533360535618378132637429718068114961380688657908494580122963258952897654000350692006139, which was once valued at USD 1000.
2. The Enigma Code

The Enigma code, a highly advanced cipher, was employed by the Germans during the Second World War. It relied on the Enigma machine, a device resembling a typewriter, where pressing a key illuminated the corresponding cipher letter on a screen. The machine featured multiple wheels connected by wires, dictating the cipher letter displayed. All Enigma machines were identical, and the initial wheel configuration was crucial for encryption. To increase complexity, the wheels rotated after a set number of keystrokes, altering the cipher mid-message. German operators received daily configuration lists to ensure uniformity. Even after the Allies obtained an Enigma machine, deciphering messages was nearly impossible due to the over one hundred trillion possible configurations. The code was ultimately cracked through Polish innovation and British expertise, leveraging both human intellect and early computing. This breakthrough provided the Allies with a critical wartime advantage and laid the groundwork for modern computers.
1. True Codes

In true codes, every word is substituted with a codeword or number based on a predefined key. Typically, this key is a codebook resembling a dictionary, where one can find the corresponding codeword for any English word. Unlike ciphers, codes require significantly longer messages before word frequency analysis becomes effective, making them more challenging to decode. Many nations have employed code variants, updating them daily to thwart frequency analysis. However, codes are impractical for everyday use due to their slow nature and the complexity of creating codebooks. If a codebook is compromised, the entire system becomes insecure, necessitating the creation of a new codebook—a time-consuming and labor-intensive process. Consequently, codes are primarily utilized by the wealthy and powerful, who can assign such tasks to others.
