Do you wish to be perceived as a computer genius and expert hacker? Since hacking necessitates extensive computer knowledge, observers are often impressed when they witness what they perceive as hacking. You don't need to engage in any illegal activities to make others think you're hacking—you can even simulate hacking using only the Windows Command Prompt (CMD) or a web browser. Continue reading for advice on appearing like a hacker through basic terminal commands and simulators.
Key Information
- Utilize Command Prompt (cmd) on Windows or Terminal on a Mac to execute non-threatening yet intimidating commands that mimic hacking.
- On Windows, you can craft a batch script that creates the appearance of hacking into a system and downloading files in real-time.
- Websites such as GeekTyper and Hacker Typer showcase authentic-looking hacker interfaces in your browser.
Procedure
Using Command Prompt or Terminal
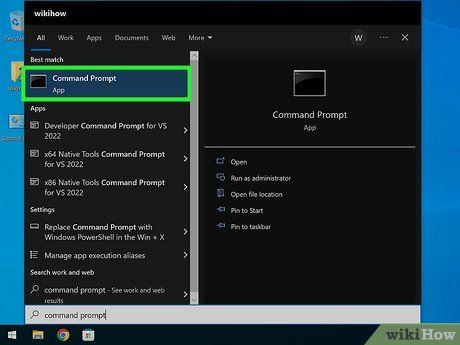
- On Windows, enter cmd in the search bar and select Command Prompt from the results.
- For Mac, go to Launchpad, search for terminal, and choose Terminal from the results.
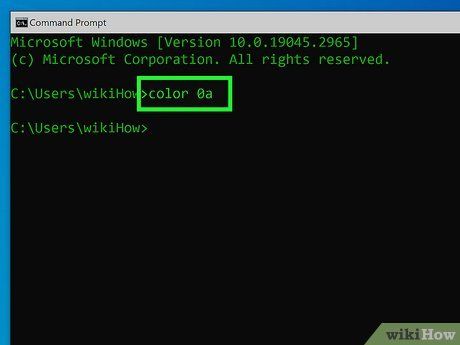
- Windows: Type color 0A and press Enter for green text on black. Use color //? to see all color options.
- Mac: Navigate to Terminal > Settings > Profiles, and choose the Homebrew profile for black background with green and blue text.
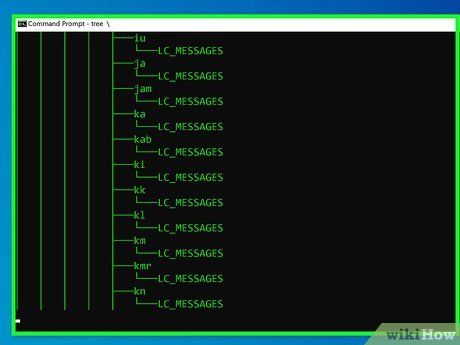
- Windows: Enter commands like tree, dir , ipconfig /all, and ping -t google.com.
- Mac: Use commands like top, ps -ely, ls -R /, and ping google.com.
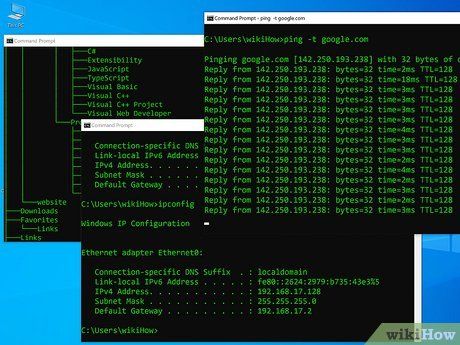
Creating a Batch File in Windows
-
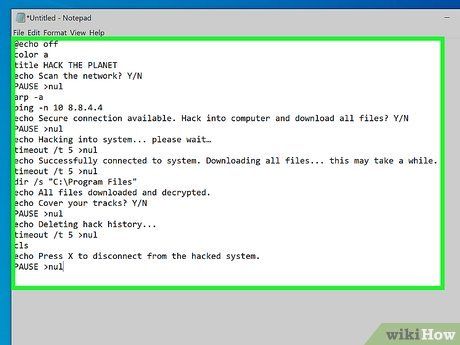
Insert the following code into your Notepad file:
@echo off
color a
title HACK THE PLANET
echo Scan the network? Y/N
PAUSE >nul
arp -a
ping -n 10 8.8.4.4
echo Secure connection available. Hack into computer and download all files? Y/N
PAUSE >nul
echo Hacking into system... please wait…
timeout /t 5 >nul
echo Successfully connected to system. Downloading all files... this may take a while.
timeout /t 5 >nul
dir /s 'C:Program Files'
echo All files downloaded and decrypted.
echo Cover your tracks? Y/N
PAUSE >nul
echo Deleting hack history...
timeout /t 5 >nul
cls
echo Press X to disconnect from the hacked system.
PAUSE >nul
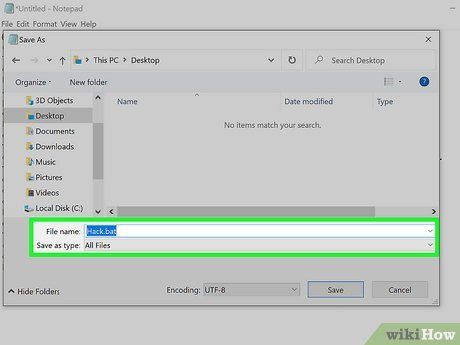
- Storing the file on your desktop simplifies execution.
- If your Windows installation isn't on the C drive, you may encounter an error. In such cases, substitute the 'C' in 'C:Program Files' with the appropriate drive letter. You can also modify this path to any folder, such as a fictitious directory containing files like 'Passwords' or 'Private Information.'
Exploring Websites
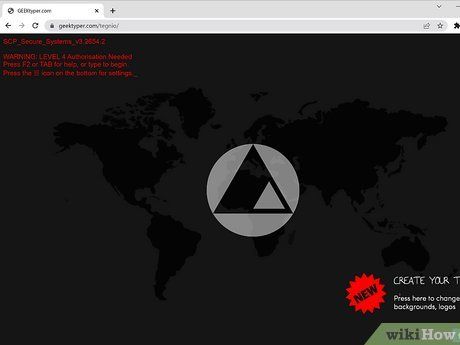
- Select a theme and navigate between the text and processes generated by keystrokes by clicking on folders and windows.
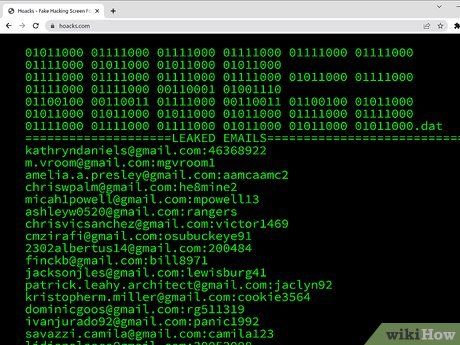
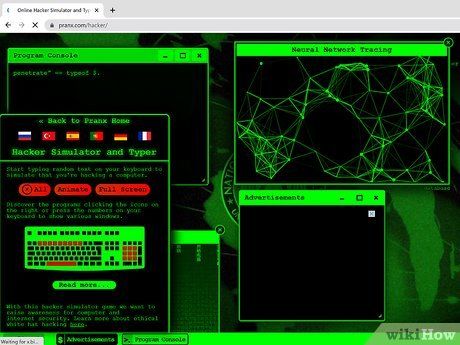
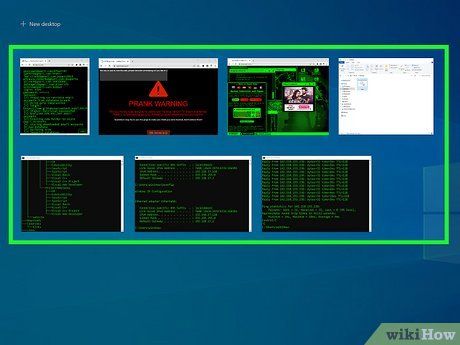
- Experiment with different window arrangements, or keep some windows open in the background to give the impression of being a skilled hacker.
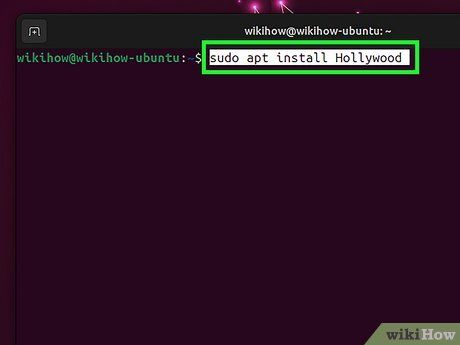
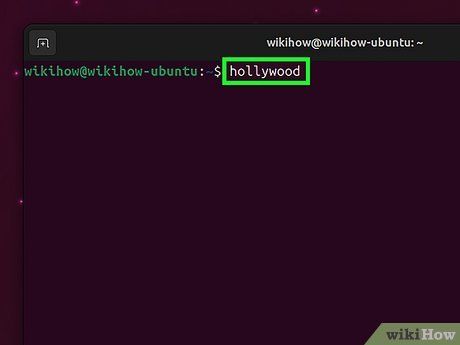
Utilizing Linux (Ubuntu & Debian)

- If Linux isn't yet installed, refer to this useful guide.
Pointers
Cautionary Notes
- Individuals knowledgeable in computer systems and coding can promptly discern whether you're genuinely engaged in activity or merely theatrics. Therefore, choose your audience for your 'hacking' demonstration wisely.
- Some adults might genuinely believe you're hacking, so exercise caution and avoid getting into trouble.
